Atomically buying digital recordsdata with digital forex is an concept that has an extended historical past on this house. Digital items, digital cash, the 2 seem to be an ideal pairing collectively. Digital items, i.e. info, are additionally huge markets. Take into consideration all of the video, audio, textual content, video games, and different types of digital content material that individuals buy and devour frequently. These are markets value billions and billions of {dollars} that individuals work together with every day.
Many of the critical makes an attempt at implementing paid file sharing have gone down unhealthy roads. Filecoin was an try to do that on high of IPFS, however finally the venture is absurdly over engineered. BitTorrent (the corporate, not the protocol) was purchased by Justin Solar and built-in its personal cryptocurrency and blockchain. Each of those tasks have successfully gone nowhere productive, with extraordinarily overengineered methods on the technical aspect, and really doubtful incentives on the financial aspect.
BitStream is a proposal by Robin Linus (ever think about slowing down and taking a break Robin?) to try to handle the necessities of atomicly buying knowledge with out the pointless addition of altcoins and over engineered technical protocols for the trade.
All recordsdata will be uniquely recognized by a single hash, it is a essential element on this scheme. Promoting a file atomically requires encrypting the file utilizing a perform that permits the consumer to confirm what’s encrypted, and after having executed so the consumer atomically purchases the encryption key for the file. The issue is the verification course of, and extra importantly proving if you happen to had been cheated and the file decrypts to incorrect knowledge, is dear. Naively executed, you would wish to supply your complete encrypted file and the decryption key so others may decrypt it and confirm the decrypted knowledge didn’t match the anticipated hash worth when hashed.
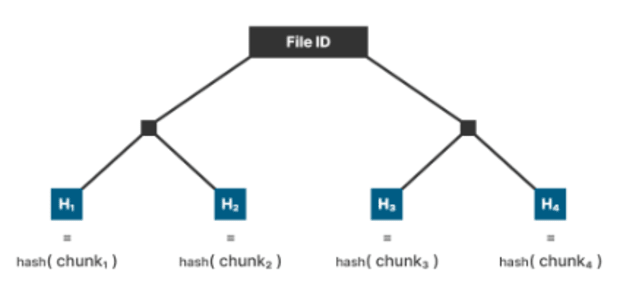
File-sharing methods like BitTorrent steadily break recordsdata up into normal sized chunks and construct a merkle tree out of them, which permits the foundation hash to perform as a file identifier in a magnet hyperlink and to confirm every particular person chunk of a file you obtain is a sound piece of that file. This can be a property that may be taken benefit of to drastically enhance the effectivity of fraud proofs exhibiting a file distributor cheated you.
The vendor of the file can generate a random worth and use this to encrypt every file chunk utilizing a XOR operation in opposition to that random worth. They’ll then signal an attestation of the encrypted file root hash and the hash of the encryption worth. The encrypted file tree is about up in a particular method to facilitate easy fraud proofs.
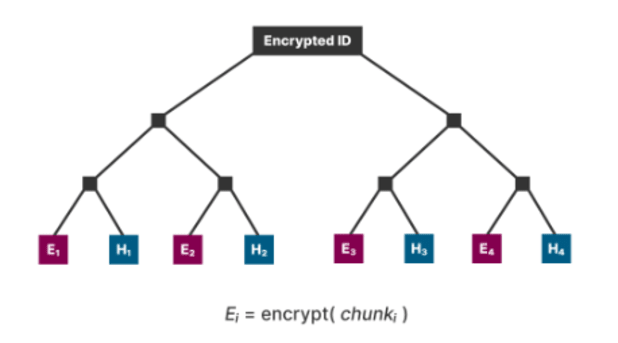
As an alternative of constructing the merkle tree out of simply the traditional file chunks, however encrypted, the tree creates pairs of leaves that consist of 1 encrypted file chunk and the hash of the unencrypted file chunk subsequent to it. Now at this level the customer can obtain the encrypted file, and after verifying by taking the entire hashes of the unencrypted chunks and making a merkle tree from them to make sure they match the foundation hash of the unencrypted file, can atomically buy the decryption worth. That is completed by the vendor utilizing it because the preimage to an HTLC over the Lightning community or a chaumian ecash mint like Cashu which helps HTLCs.
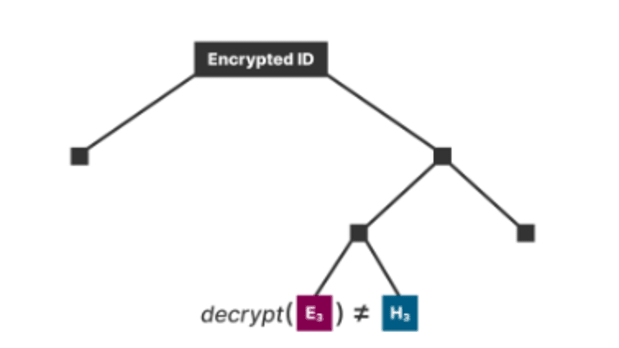
If the file doesn’t decrypt appropriately, both as a result of the encrypted knowledge is a special file or the preimage just isn’t the precise encryption key, the merkle path within the encrypted file tree to any two leaves can present the vendor cheated the customer. Offering simply the trail to any encrypted file chunk and its corresponding unencrypted chunk hash with the preimage the customer bought will show definitively the vendor didn’t present the customer with the file they claimed they had been.
Any file vendor utilizing the BitStream protocol can deposit a bond that may be slashed with a fraud proof as designed above in the event that they cheat a buyer. This may be enforced by merely depositing a bond at a chaumian mint within the easiest case. Platforms like Liquid supply various strategies of constructing a bond that may truly be enforced trustlessly with performance like OP_CAT. Scripts might be constructed that truly take the BitStream fraud proof and validate it on the stack, permitting the creation of a UTXO that may be spendable by anybody who had a sound fraud proof. If OP_CAT ever grew to become obtainable on the mainchain, this might even be executed fully trustlessly without having a federated execution atmosphere.
BitStream is an extremely promising protocol for atomically promoting digital info with a really environment friendly scheme for proving fraud, no shitcoins required.






More NFT News
High Trending Cryptos on Solana Chain At present – Jiji, Buna, Popcat
Will They Mine Or Maul It?
It is Time To Swap Your {Dollars} For Bitcoin